Vulcan Cyber Endpoint Vulnerability and Risk Management
Buy on CrowdStrike Marketplace
This product is available from CrowdStrike — it may even qualify for CrowdCredits.
Vulnerability remediation orchestration
Vulcan Cyber gives you the tools to effectively manage the vulnerability and risk lifecycle for your cyber assets, including application, cloud, and infrastructure. By integrating with your tools, including the CrowdStrike Falcon® platform, you can better analyze and prioritize your vulnerability and risk data to orchestrate remediation. Playbooks automate communication and collaboration between teams responsible for mitigation and execute remediation actions when appropriate. With Vulcan Cyber and CrowdStrike Falcon you can easily manage the cyber risk lifecycle for endpoints and cloud assets, use rich CrowdStrike security data to analyze and prioritize vulnerabilities based on your risk profile, and facilitate communication and collaboration between all departments. With this integration, your team is empowered to better understand endpoint risks and fixes through customizable dashboards, visualizations, and reports.
- 01
Automated vulnerability and risk prioritization and mitigation
Prioritize which vulnerabilities you should address first and deliver the right fix or workaround solution with expert-defined context to minimize risk and strengthen your security posture.
- 02
Rapid vulnerability and risk mitigation for better collaboration between departments
Automatically communicate vulnerabilities, fix details, and track progress.
- 03
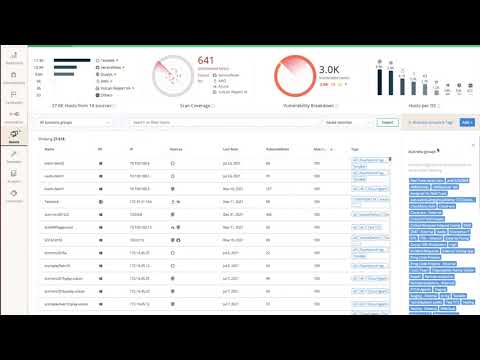
Comprehensive tracking and reporting
Gather deep analytics for any audience to demonstrate how well your vulnerability and risk management efforts are working.
- 04
Improved cyber risk awareness
Centralize, analyze and correlate vulnerability and risk data for deeper visibility into actual risk and its potential impact.