Actively defending the enterprise of things
Increase compliance and maximize threat defense by capitalizing on Forescout’s continuous enterprise-wide device visibility and automated workflows integrated with CrowdStrike. The Forescout® eyeExtend for CrowdStrike module orchestrates information sharing and security workflows between Forescout and CrowdStrike to improve device hygiene, proactively detect threats across the network and automate threat response.
The integrated solution combines the agentless visibility and control capabilities of the Forescout Platform with the threat intelligence and advanced endpoint protection of the CrowdStrike Falcon® platform.
- 01
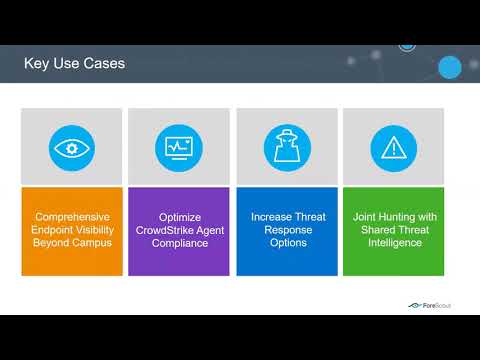
Improve device security coverage and compliance
Forescout continuously verifies that the CrowdStrike agent is installed and running on supported devices and communicating properly with the CrowdStrike cloud. After determining if a device is new, unmanaged or has a broken agent, Forescout notifiesthe administrators and facilitates remediation by redirecting users to a self-help page for agent installation. Devices that leave the network are verified when they reconnect to enforce compliance.
- 02
Improve insight into corporate devices on-site or off-premises
Forescout eyeExtend powered by Forescout eyeSight provides comprehensive visibility across all networked attached devices agentlessly. The Forescout platform also pulls device information on CrowdStrike managed devices while those devices are on-site or off the enterprise network, providing you with a more comprehensive device inventory.
- 03
Leverage shared threat intelligence to maximize joint threat hunting and detection
CrowdStrike identifies malware and Indicators of Attacks (IOAs) on managed devices and notifies Forescout eyeExtend upon detection. Forescout leverages this threat intelligence to monitor the network for IOAs across unmanaged devices such as BYOD, guest and IoT, as well as network infrastructure. Based on your policy, the Forescout platform can limit network access for compromised devices dynamically.
- 04
Accelerate and automate policy-driven threat response
Upon detection of malware or malicious behavior, CrowdStrike immediately informs Forescout eyeExtend. Based on threat type and your policies, the Forescout platform automatically takes appropriate network control actions such as restricting or blocking compromised devices in real time. If an on- or off-prem device is found to be infected, CrowdStrike can trigger the Forescout platform to dynamically isolate the device and contain the threat by cutting off all network access except for its access to the CrowdStrike server for remediation. Forescout’s network control actions reduce your mean time to respond (MTTR) and limit the impact of threats.