Learn about device trust with StrongDM
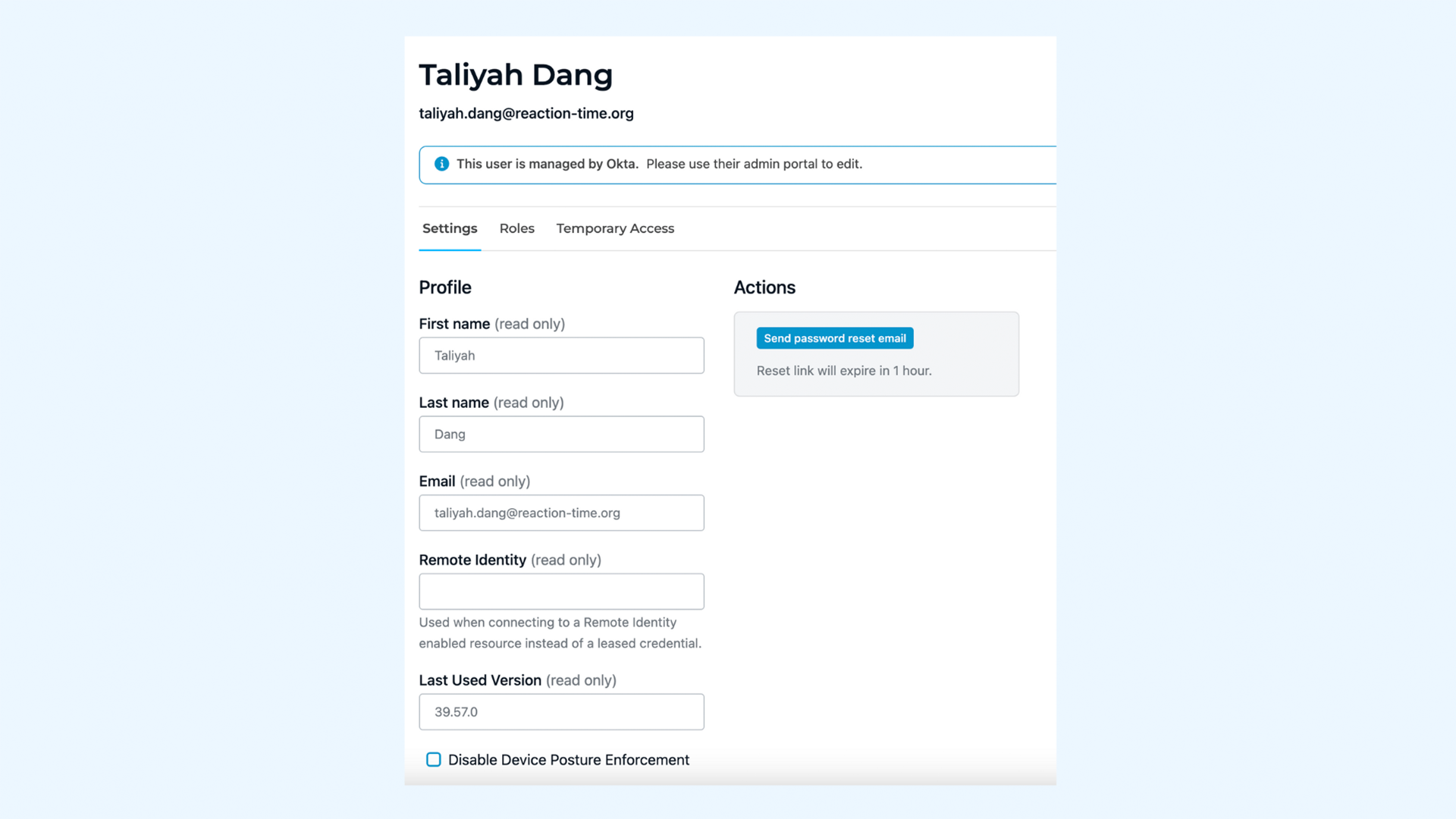
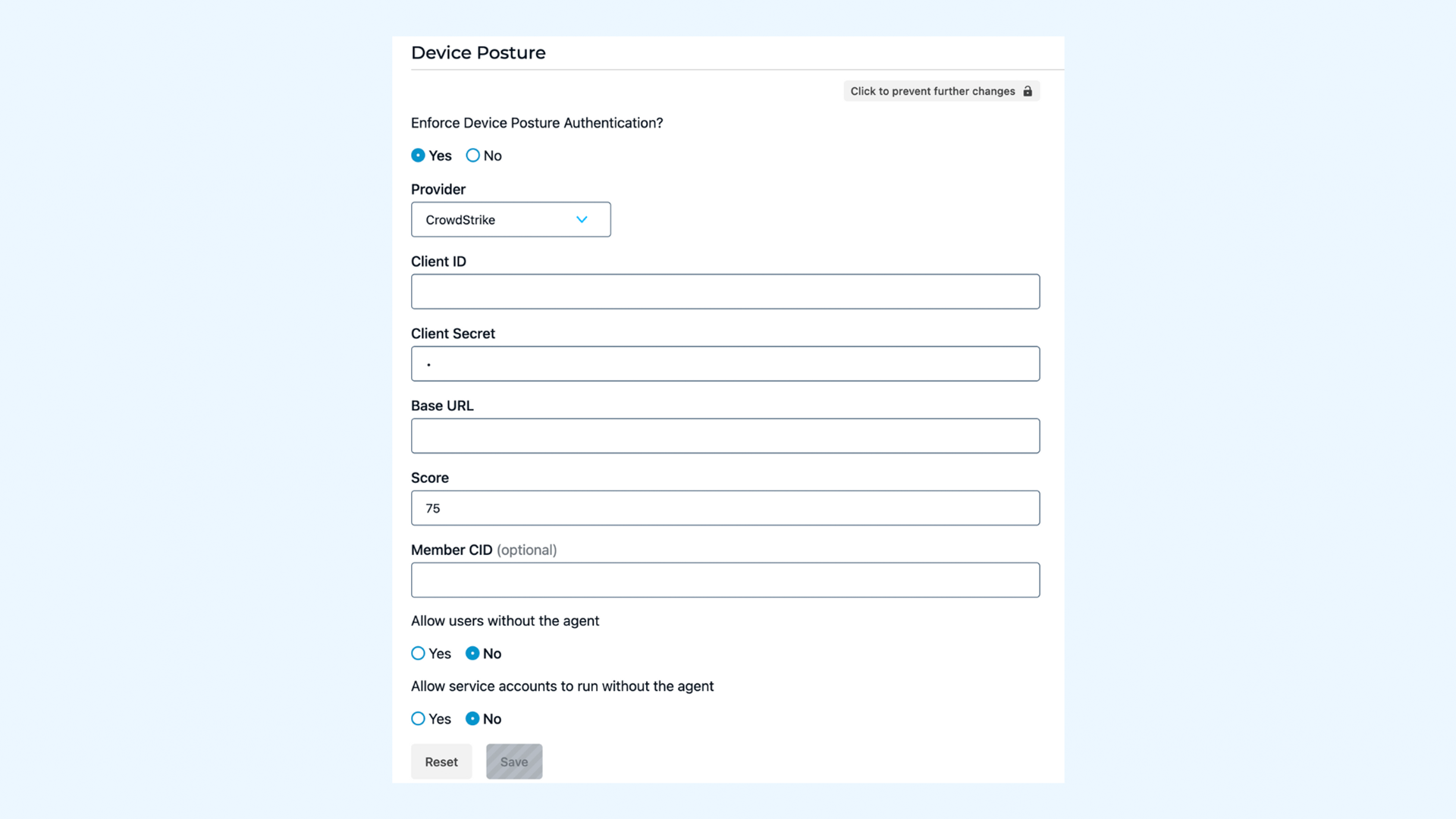
StrongDM grants dynamic access to critical infrastructure, including databases, clouds, servers, clusters, and web applications. Access is granted only after authenticated and authorized for that resource. Combining StrongDM with CrowdStrike’s rich endpoint insights, your team gains additional context for every access request, including the risk profile of the device the person is using. Trust the user, trust the device, and then grant access. With continuous risk assessment, access can be severed at any time.
- 01
Context-based infrastructure access
Know exactly who is accessing critical infrastructure, from where, and what device. StrongDM combines access insights with device risk signals from CrowdStrike to determine whether access should be granted
- 02
Continuous risk-based assessment
Constantly evaluate device health at regular intervals to ensure connections are still valid, improving your security posture
- 03
Reduce the attack surface
Automatically deny or revoke access to devices that are at high risk, mitigating unauthorized access and potential threats
- 04
Dynamic security policy
Adjust StrongDM security policies to be stricter or more relaxed based on CrowdStrike’s insights on device posture to boost operations based on your unique needs