Your security stack is getting heavy; Let Monad lighten the load
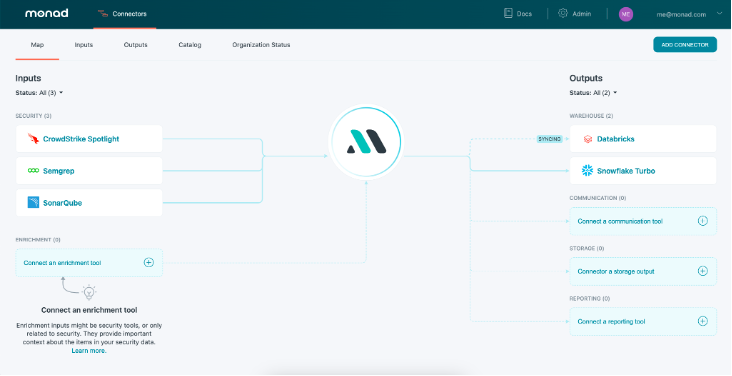
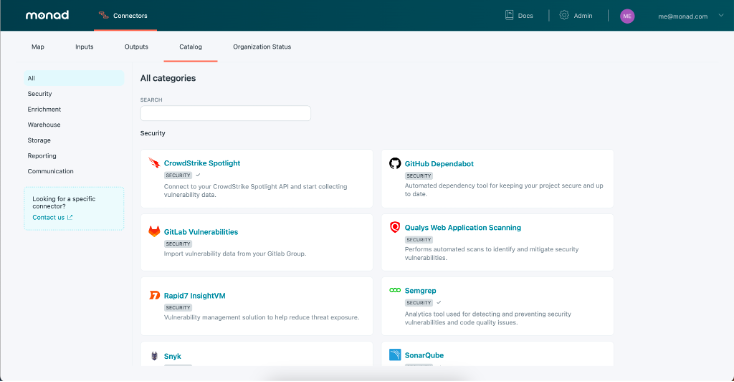
Say goodbye to traditional vulnerability management and say hello to CrowdStrike Falcon® Spotlight + Monad. Today’s enterprises use dozens of security tools, but lack the infrastructure required to ingest, transform, and make sense of the data from these tools. Monad provides this infrastructure. With Monad and Falcon Spotlight, you can quickly and easily combine CrowdStrike vulnerability findings with security data from elsewhere in the organization, increasing visibility and decreasing response times.
- 01
Robust data ingestion
Monad’s security data ingestion pipelines conduct rich, structured data ingestion for enterprise-scale workloads across CrowdStrike and other disparate security data sources
- 02
Flexible data modeling
Get flexibility and control over the format of your security data with models that fit your needs
- 03
Portable data export
Export normalized and transformed data including CrowdStrike security data to your preferred location for deeper analysis and insights