Legit Security Platform
Application security and traceability from code to cloud
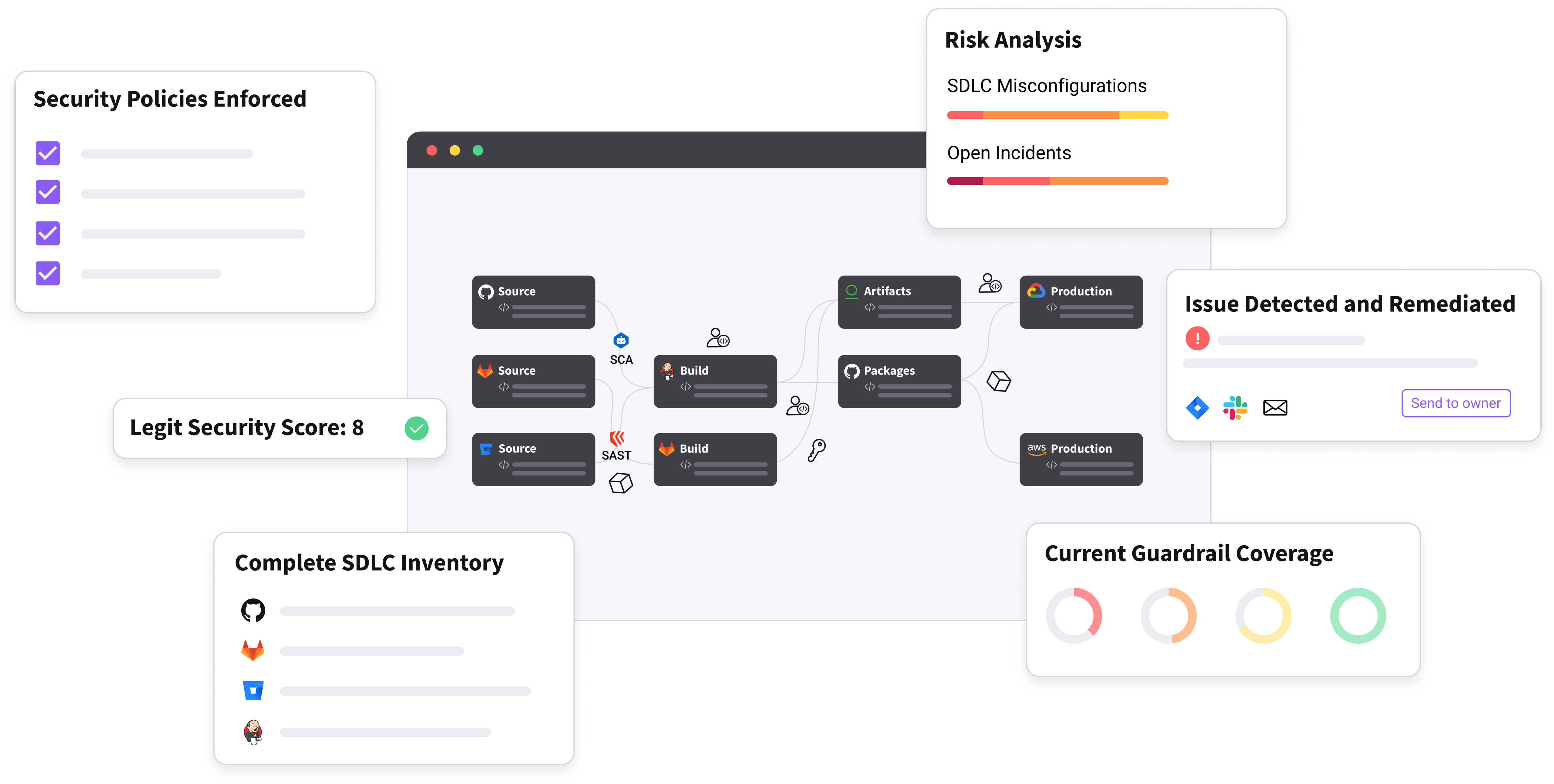
Legit Security integrates with the CrowdStrike Falcon® platform to auto-discover, analyze and secure applications from code to cloud. Organizations can automatically trace cloud application vulnerabilities back to their origin and any development vulnerabilities to production environments, improving visibility for faster, more efficient vulnerability remediation. Legit Security ingests enriched security data across managed cloud workloads from the Falcon platform to identify the source of vulnerabilities, trace it back to the development owner, triage and prioritize issues based on severity, and provide rich context to remediate issues and fortify application security at speed.
- 01
Code to cloud traceability and security
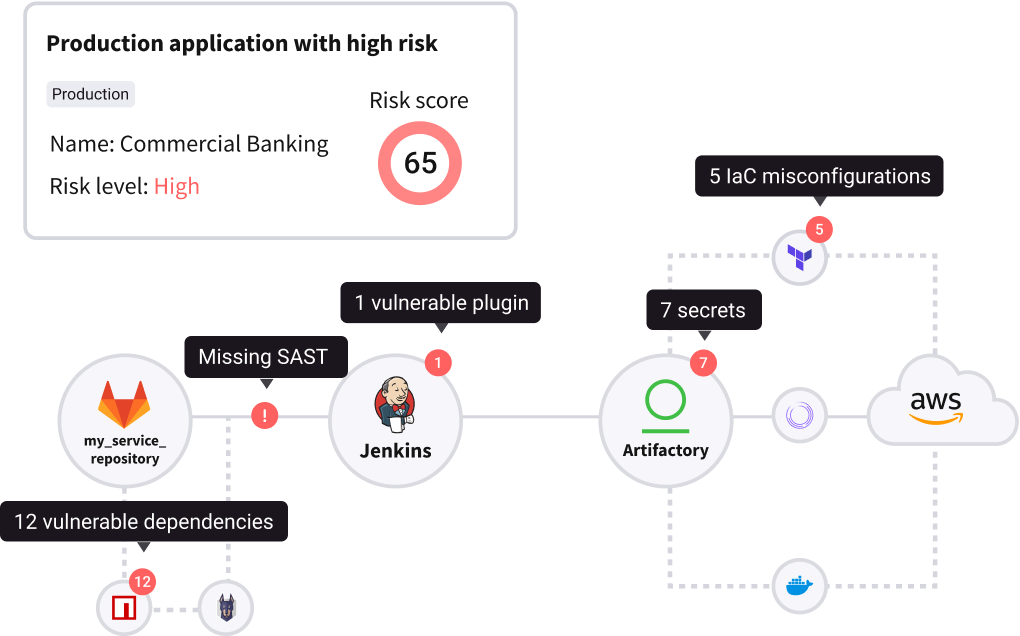
Rapidly identify and remediate application risks with forensic detail and traceability from code origin to cloud vulnerability to improve TTR, productivity, and threat prioritization.
- 02
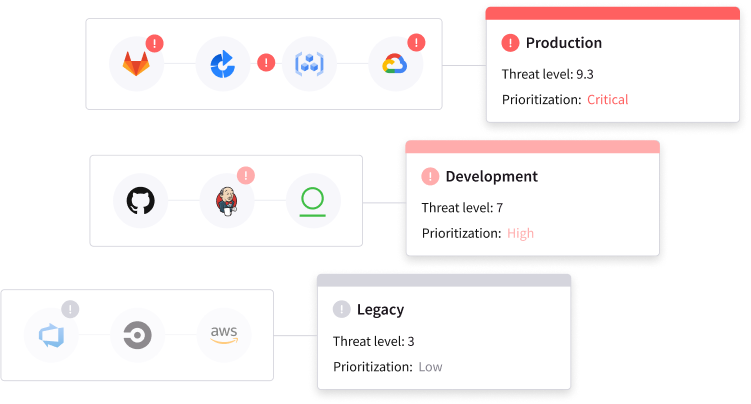
Application security control plane
Simplify application security enforcement with centralized security policies, risk scoring, and consolidated AppSec vulnerability management.
- 03
Software supply chain security
Protect against increasing attacks with software development life cycle (SDLC) auto discovery and analysis, CI/CD pipeline security, and secrets detection in code.
- 04
Continuous compliance and software bill of materials (SBOM)
Align regulatory compliance to security guardrails and provide continuous assurance, compliance drift detection, and SBOM creation.