ArcSight Intelligence
World-class behavioral analytics for a safer, more secure organization
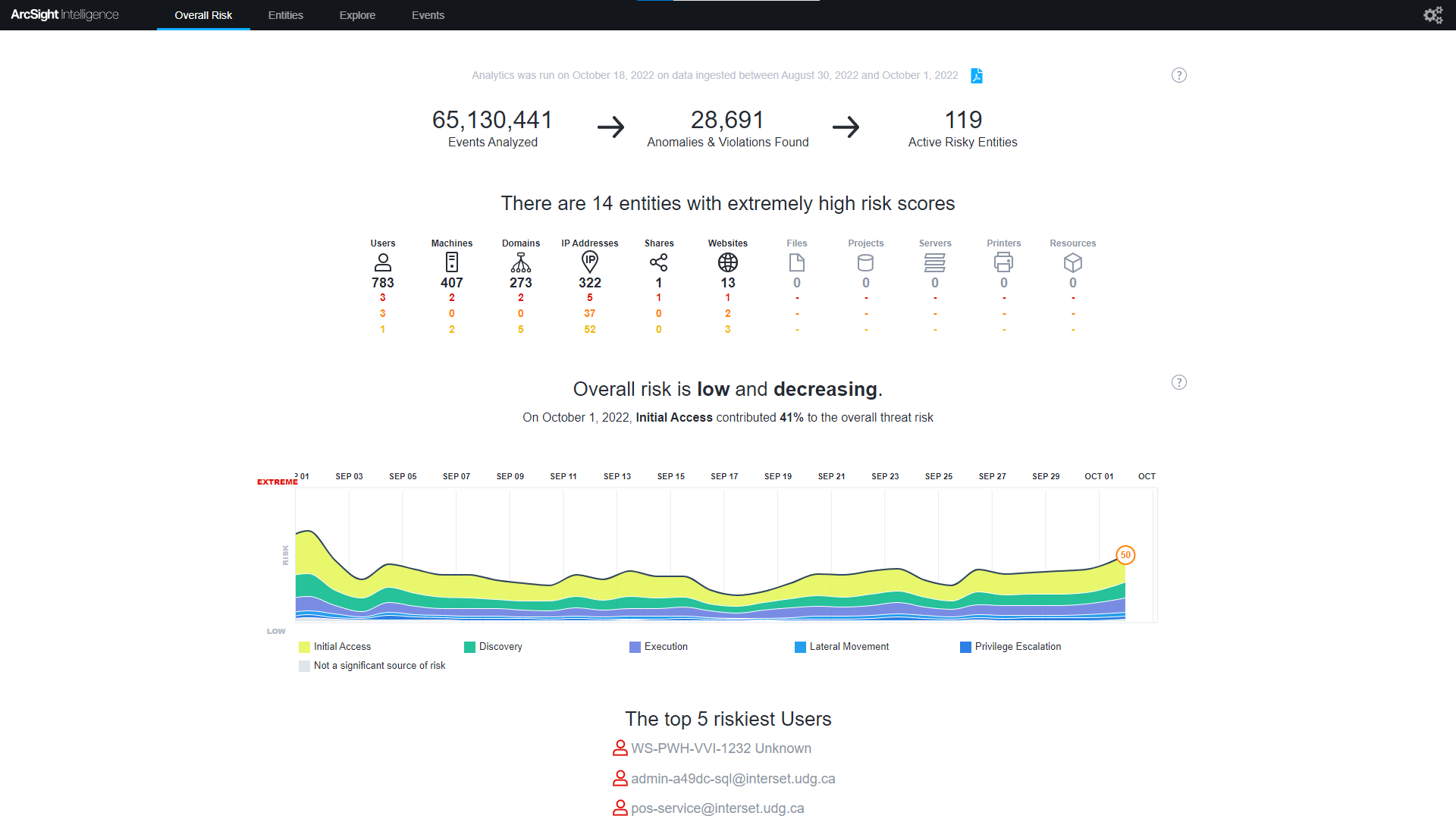
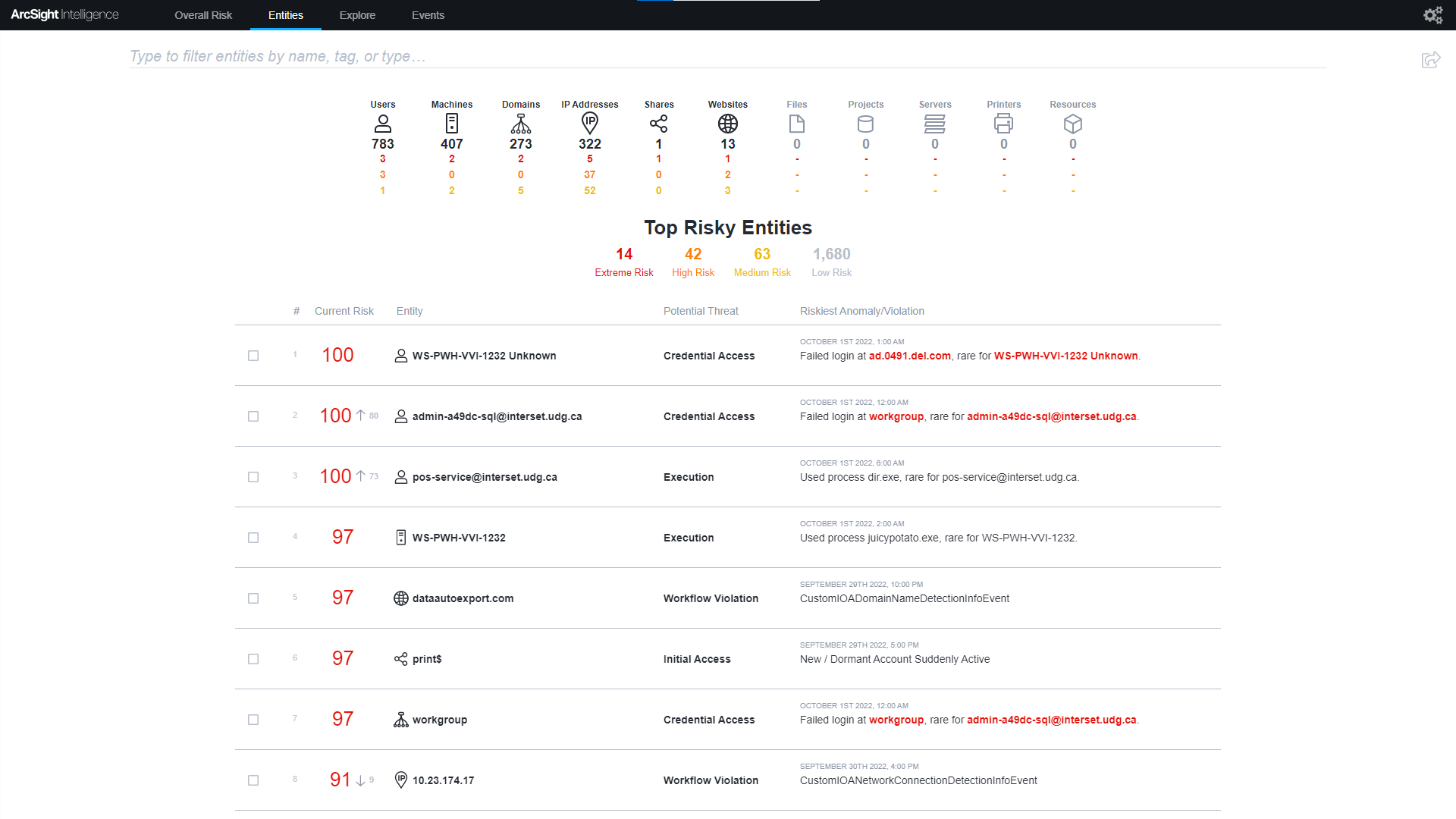
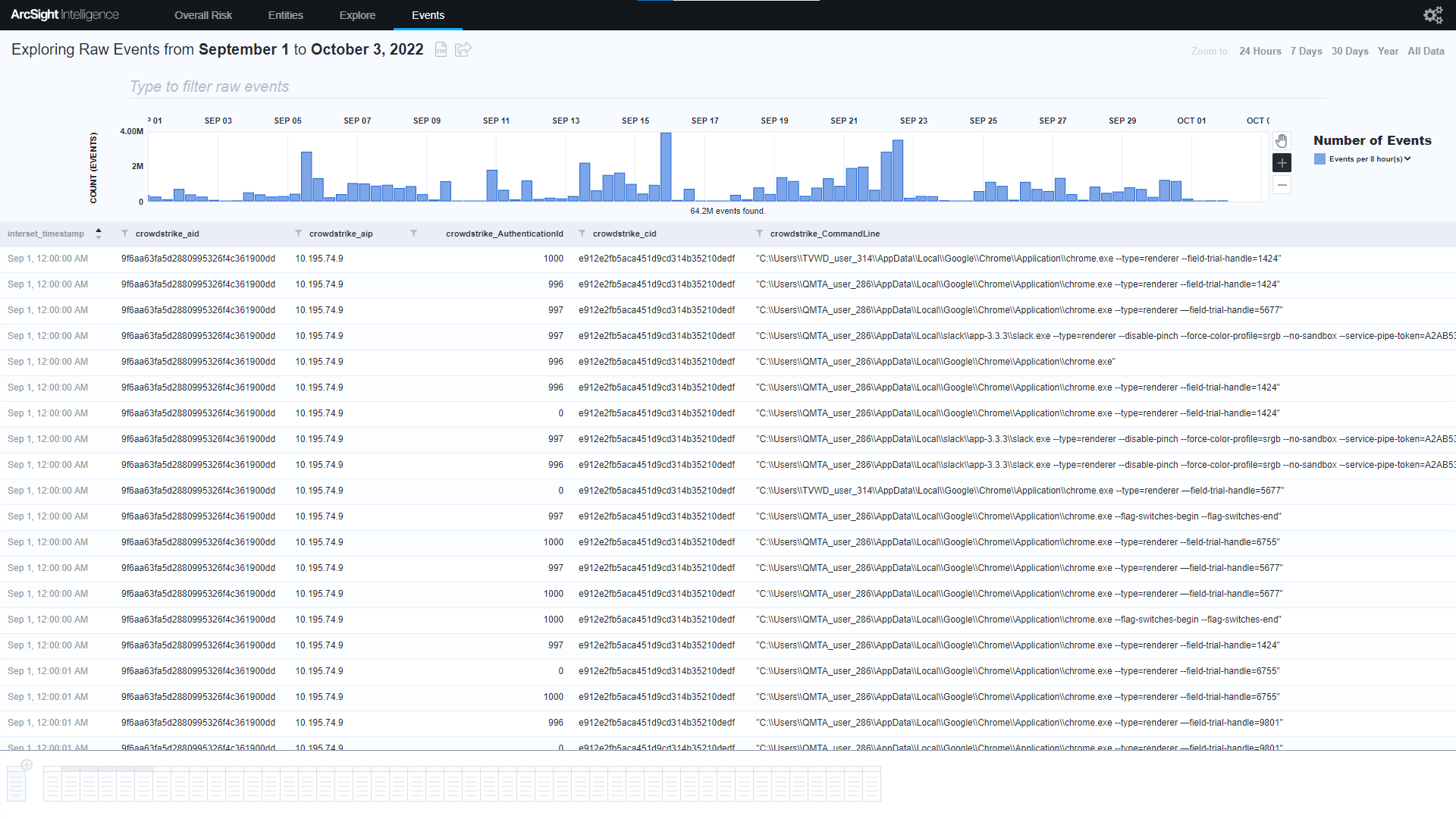
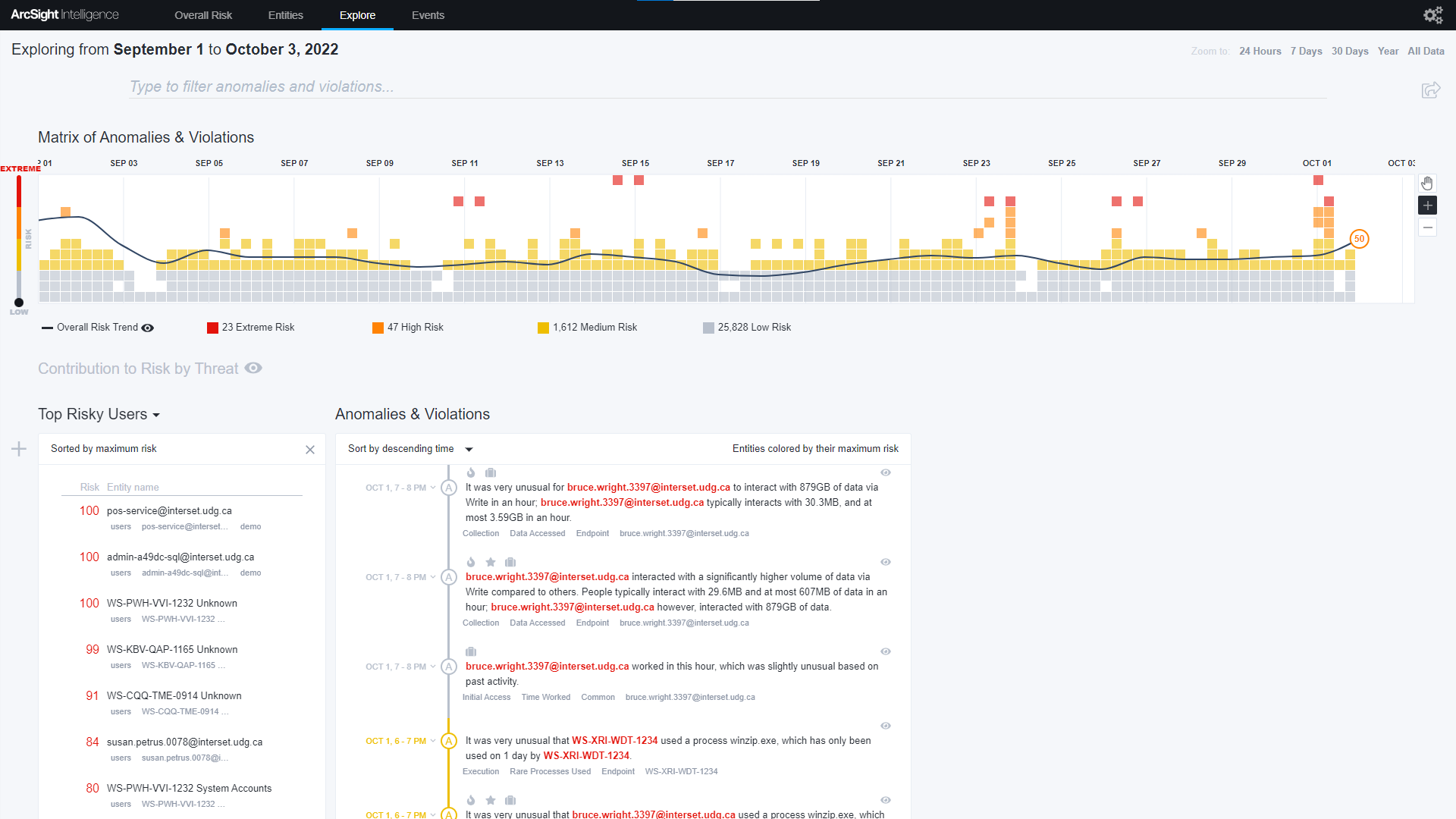
ArcSight Intelligence’s UEBA engine uses unsupervised machine learning and expanded behavioral analytics models on your CrowdStrike Falcon® data to detect insider threats, critical vulnerabilities, compromised accounts, lateral movement, internal recon, or data exfiltration to reduce dwell time. Utilize the power of unsupervised machine learning to discover the "unique normal" baseline of every user, machine, and entity in your organization. ArcSight Intelligence automatically leverages your organization's baseline to detect hard to find suspicious activity in your organization’s blind spots that may indicate potential threats.
- 01
Detect insider threats and anomalous activity
Utilize the power of unsupervised machine learning to discover the "unique normal" baseline of every user, machine, and entity in your organization to detect hard to find suspicious activity in your organization’s blind spots that may indicate potential threats from a variety of methods including insider threats, lateral movement, and living-off-the-land attacks.
- 02
Streamline user experience and threat investigation
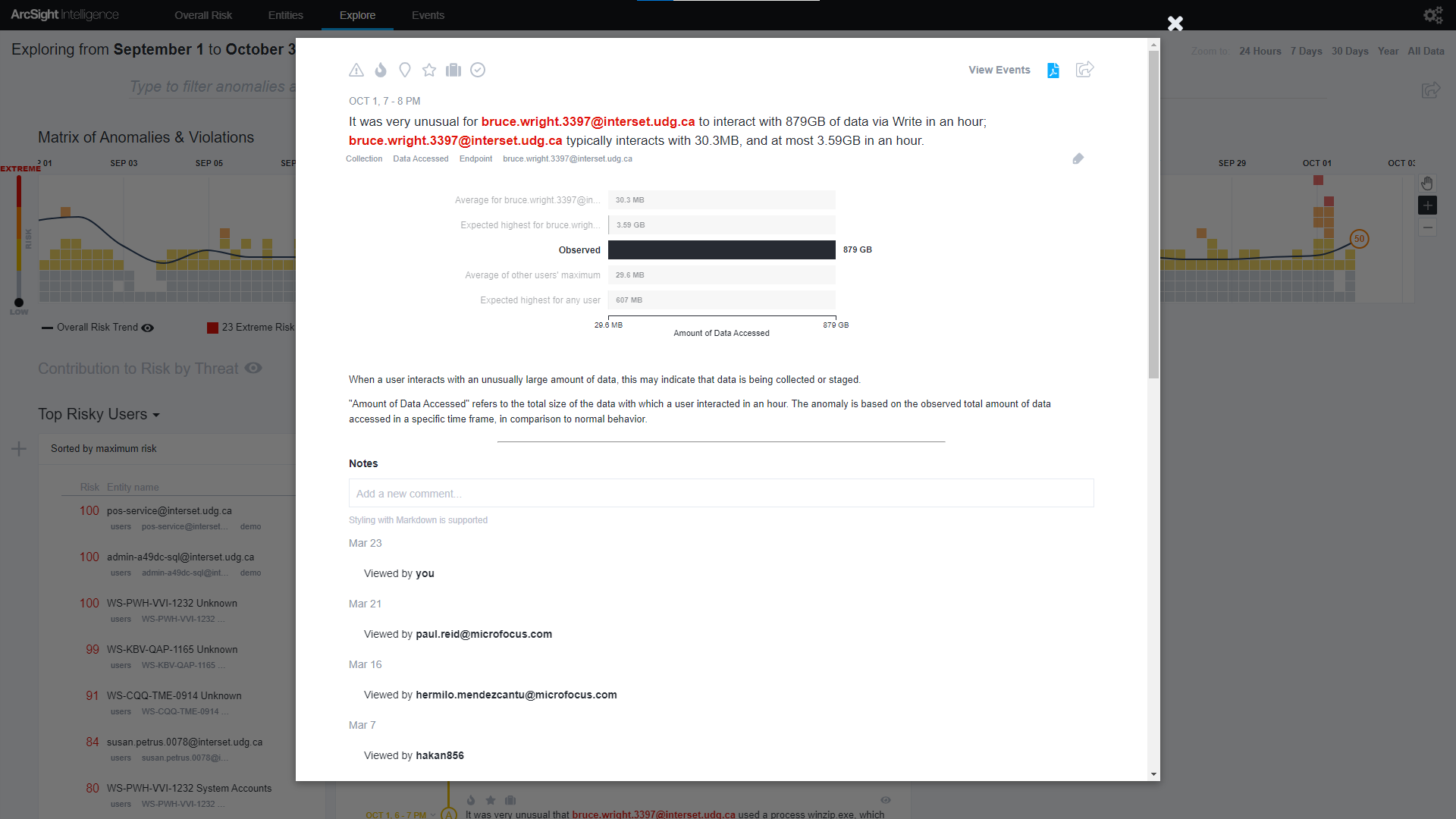
At ArcSight, we built an intuitive user interface that enables analysts to see at a glance the state of their organization's security. Not only that, but we have ensured that analysts will not be bottlenecked by slow data pulls by creating speed-of-thought threat hunting capabilities.
- 03
Gain world-class behavioral threat hunting as a service
As an addition to your in-house or third-party threat hunting services, ArcSight Intelligence offers insightful threat hunting readouts free of charge for free trials and supplementary threat hunting afterwards as an optional paid service. This service specializes in finding threats without set rules from attack types such as insider threats, lateral movement, and more.