Beyond Identity Zero Trust Authentication
Identity and device assurance for continuous, risk-based authentication
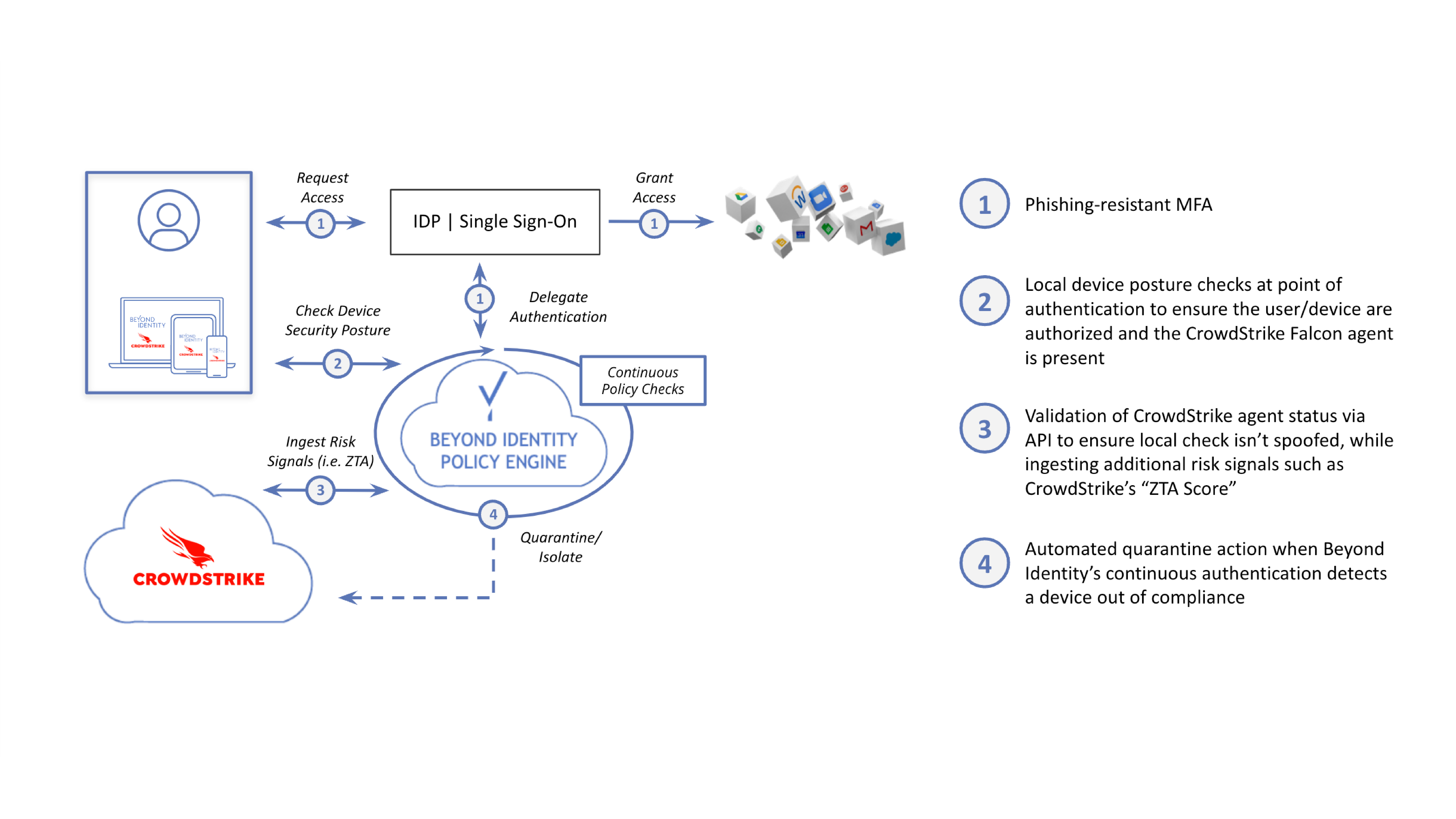
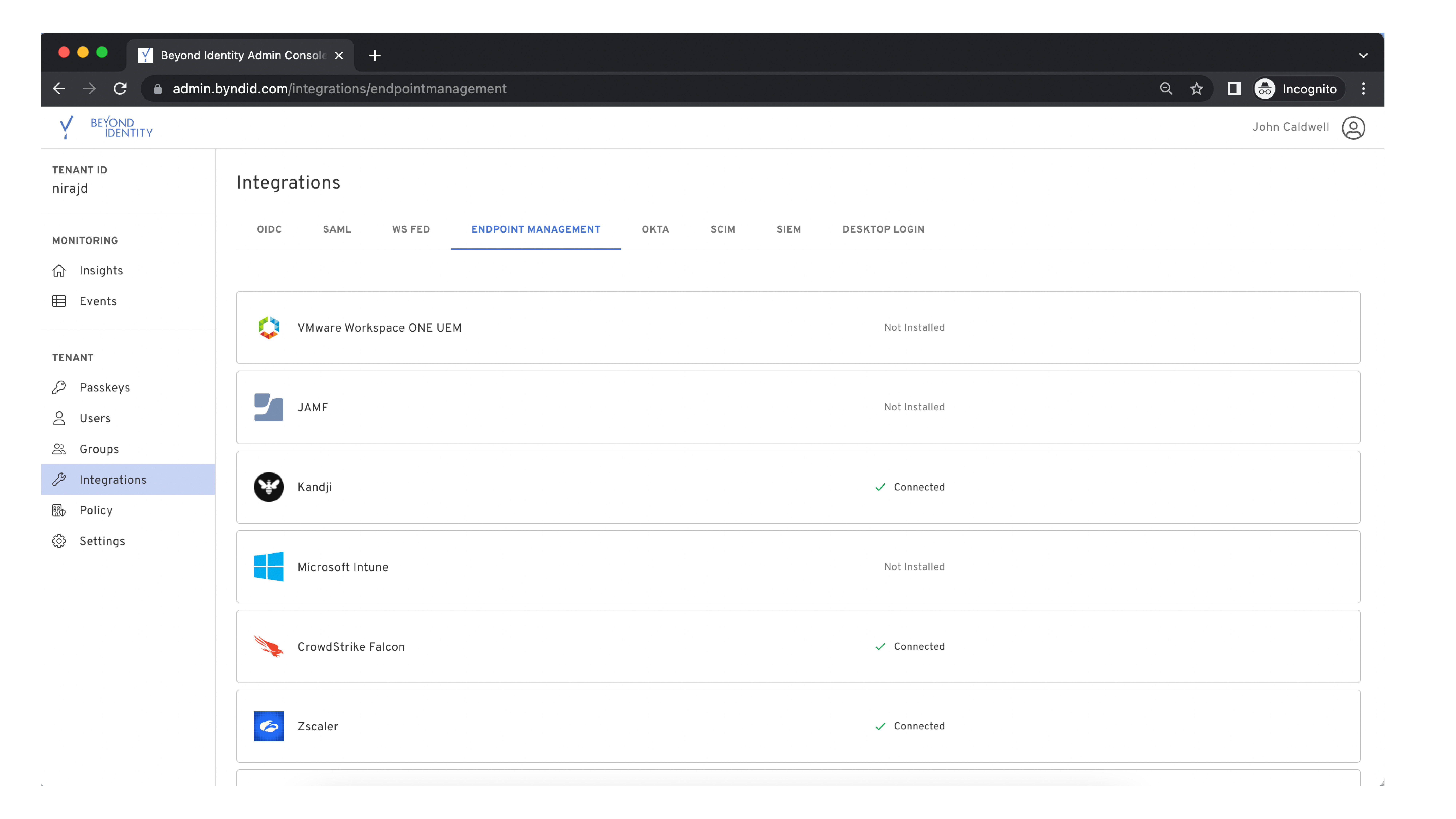
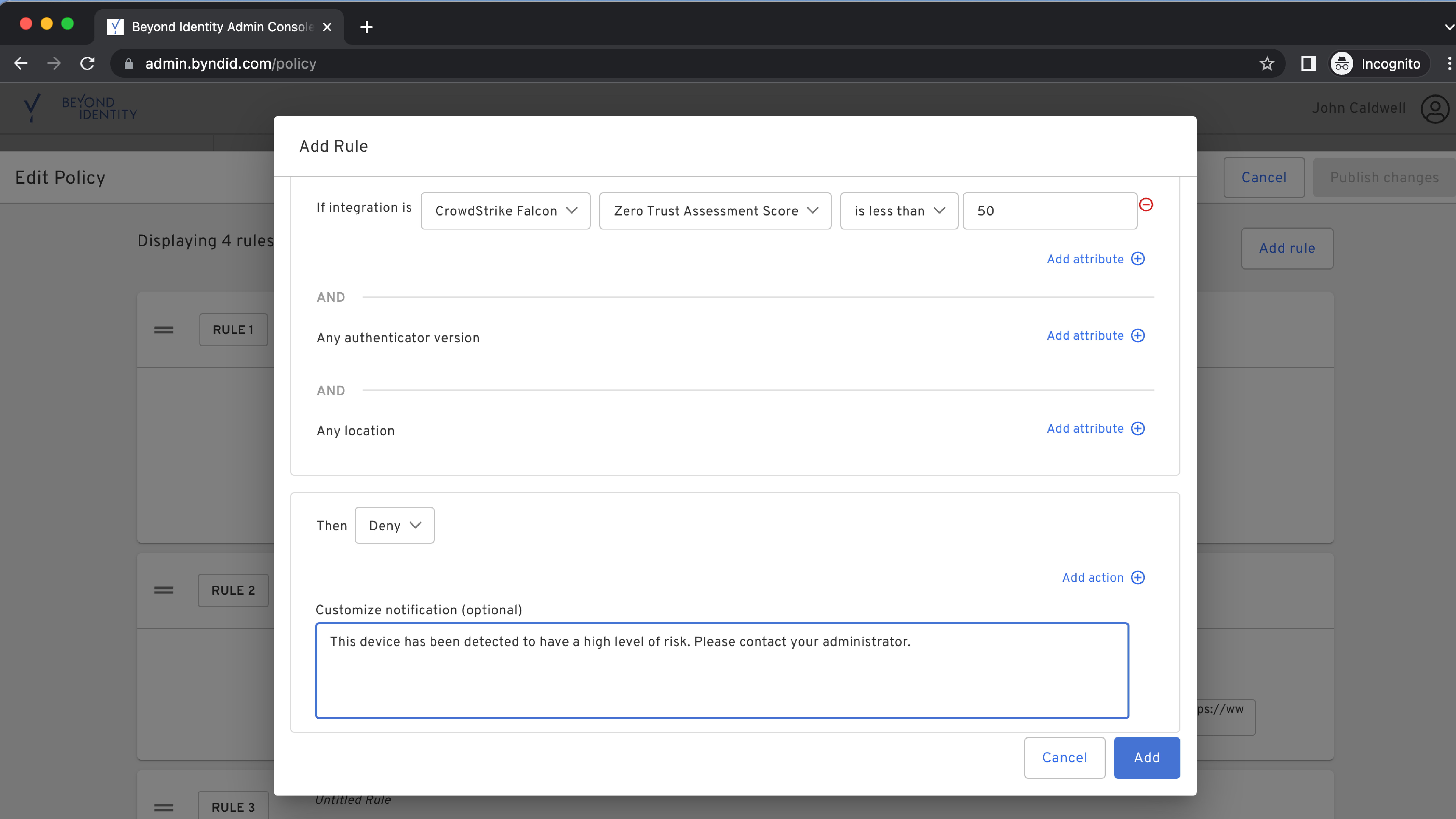
Beyond Identity is a technology innovator in the Zero Trust Authentication space by providing strong identity validation via phishing-resistant multi-factor authentication (MFA), device trust validation based on granular risk telemetry, and continuous device posture checks and policy enforcement.The Beyond Identity integration with the CrowdStrike Falcon® platform augments an organization’s ability to enforce device trust by validating the presence of the Falcon agent on the endpoint and ingesting CrowdStrike user and device risk signals derived from CrowdStrike Falcon Zero Trust Assessment (ZTA) scores. In this way, organizations can monitor and ensure adherence to precise authorization policies throughout a session, quarantining devices that fall out of compliance.
- 01
Device trust
Validate the security posture of the authenticating device to ensure only compliant, low-risk devices with the Falcon agent gain access.
- 02
Continuous authentication
Continuously evaluate identity and device trust, and quarantine non-compliant devices.
- 03
Passwordless
Prevent stolen credentials and simplify users’ experiences by replacing passwords.
- 04
Zero trust
Establish a fundamental building block of Zero Trust with phishing-resistant, effortless MFA.